Privileged remote
The term “privileged remote” generally describes the safe remote access and management of privileged accounts and systems, allowing authorized workers to carry out essential administrative functions without jeopardizing security. In IT and cybersecurity operations, where privileged accounts have enhanced access rights that could be exploited to cause serious security breaches or compromises to systems, this technique is essential. Organizations can strictly regulate who has access to privileged accounts and systems, keep a tight eye on their activities, and impose robust authentication and authorization procedures to safeguard sensitive data by putting privileged remote access solutions into place.

YouTube
Just in Time Permissions Explained #Delinea #PAM #CyberSecurity
Privileged Credential Activity Reporting Services
Scheduled Reports
- Creating New Schedules for Reports To create a schedule for a report, click the Schedules tab on the Report View page: Click the Create Schedule button.
Creating and Editing Reports
- There are two ways to create a Report. From the Reports Edit page, click the Add New link at the bottom of a Report Category.
Built-in Reports
- Secret Server includes many pre-configured reports that you can run or use as templates for creating custom reports.

As version 7.0, Secret Server allows creation of Reports using custom SQL.
Reports Overview
The reporting interface comes with a set of standard reports. These reports include a variety of 2D and 3D charting and graphing components and a full grid of data. Some of the reports are purely data detailed and have no charts.
Audits and Reports
Before running reports and audits, you must create something to report
on—to that end: Import a few accounts or create secrets manually Rotate passwords a few times View a couple of your secrets This generates enough audit logs to provide meaningful outputs in your reports: Security Hardening Repor.
Click the Reports menu item. The Reports page appears: Click the link for the desired report. Its page appears: Click the button in the top right of the item table.
Audit Reports
In addition to the user audit and individual secret audit, the reporting feature provides a series of activity, user, and secret reports.
Viewing Auditing for a Report
To view auditing for all actions performed on a report, do the following: Click Reports from the left navigation panel.
If there are requirements around protecting potentially personally identifying information when running reports or viewing recorded sessions, you can enforce that another user has authorized you by enabling dual control for a secret or Report.
Viewing a User Audit Report
To view a user audit report: From the Reports page, click the User Audit tab. From the dialog on the tab, select a user and a date range to view.
Secret Server Telemetry
Overview There are 3 reasons for Delinea products to call home—when:
Checking for available updates Activating licenses Reporting anonymized usage metrics Each of these communications is explained below and can be disabled or avoided. Checking for and Downloading Updates Frequency: Once per day The…
This topic is a one-stop resource for Secret Server developers. It points to topics, as well as legacy knowledgebase articles.
Auditing Overview
Secret Server provides comprehensive auditing features to help
organizations meet regulatory requirements and ensure security
compliance.
Features
Secret Server On-Premises Features by Version General Access Control See Gain control over web apps and cloud management platforms for more information.
Overview Secret Server uses role-based access control (RBAC) to regulate permissions. The roles are assigned to users or groups.
Secret Server Cloud
Secret Server Cloud is a scalable, multi-tenant cloud platform that offers the same robust features as the on-premise Secret Server Professional edition.
Using Dynamic Parameters in Reports
- As version 7.0, Secret Server allows creation of Reports using custom SQL.
- Reports Overview
- Audits and Reports
Saving Reports to File
- Click the Reports menu item. The Reports page appears: Click the link for the desired report.
- Audit Reports
- Viewing Auditing for a Report
Reporting and Dual Controls
- If there are requirements around protecting potentially personally identifying information when running reports or viewing recorded sessions.
- Viewing a User Audit Report
- Secret Server Telemetry
Developer Resources
- This topic is a one-stop resource for Secret Server developers. It points to topics, as well as legacy knowledgebase articles.
- Auditing Overview
- Features
Secret Server Role Permissions List
- Overview Secret Server uses role-based access control (RBAC) to regulate permissions.
- Secret Server Cloud
Introduction
Being a cybersecurity administrator in today’s fast-paced IT landscape is like being a firefighter in a city built entirely of matchsticks.

Embrace Automation—Your Best Friend :
Survival Tips: Automate provisioning and deprovisioning of privileged accounts to eliminate stale credentials. (Who: Delinea |Product: Platform, Secret Server, IGA | Benefit: Reduces
manual effort, ensures compliance)
Master the Art of Least Privilege
Why It Matters: Implement Role-Based Access Control (RBAC) to ensure users have only the access they require. (Who: Delinea |
Product: IGA, Secret Server, Server Suite | Benefit: Reduces
risk of insider threats, enforces least privilege)
Streamline Access Requests and Approvals
Implement self-service access requests with built-in
security policies. (Who: Delinea | Product: Platform, IGA,
Privileged Access Service, Secret Server | Benefit: Reduces
admin workload, improves response times)
Monitor, Detect, and Respond in Real-Time
Survival Tips: Enable session recording and keystroke logging for all
privileged sessions. (Who: Delinea | Product: Platform, Secret
Server | Benefit: Provides full accountability, aids in forensic
analysis)
Tame Third-Party and Non-Human Identities
Survival Tips: Use vendor privileged access management (VPAM) to grant temporary, monitored access. (Who: Delinea | Product:
Platform, Privileged Remote Access, Secret Server | Benefit:
Ensures secure vendor access, reduces insider risk)
Keep Compliance in Check Without Losing Your Mind
Survival Tips: Automate audit reporting to generate compliance reports on demand. (Who: Delinea | Product: Platform, Secret Server, IGA | Benefit: Saves time, simplifies audits)Survival Tips:

Don't Just Survive—Thrive!
Survival Tips: Regularly review and optimize your PAM strategy to align with evolving threats. (Who: Delinea | Product: Platform, Secret Server, AIDA | Benefit: Keeps security current, enhances threat resilience)
Final Thoughts
Managing privileged access doesn’t have to be an overwhelming task. By following these survival tips, you can secure your environment while staying sane in the process. Cybersecurity is a marathon, not a sprint—so pace yourself, automate where possible, and always stay one step ahead of attackers. Happy securing!
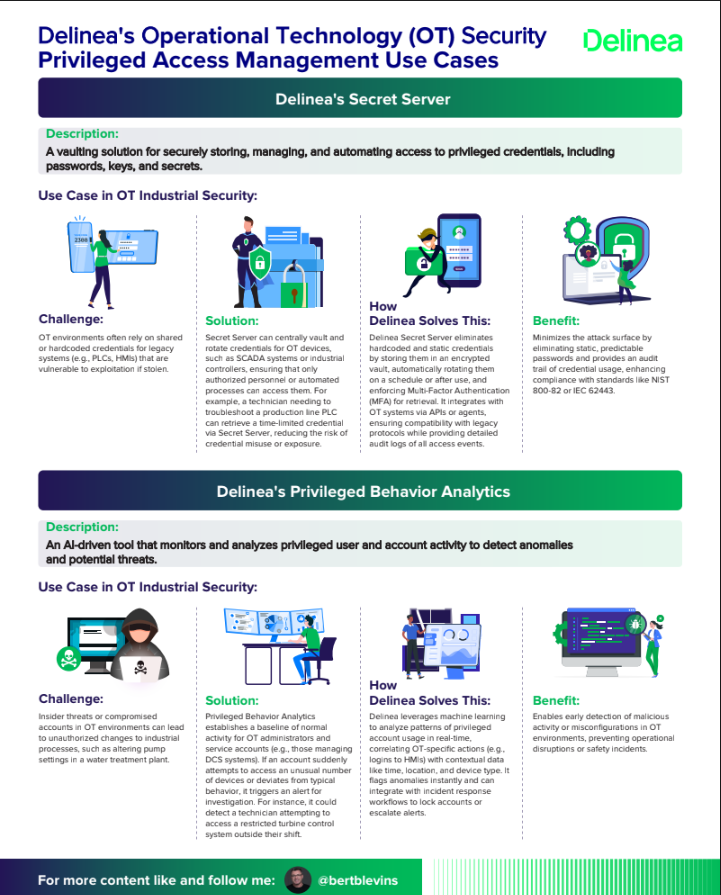
Delinea's Operational Technology (OT) Security Privileged Access Management Use Cases
Challenge: OT environments often rely on shared or hardcoded credentials for legacy systems (e.g., PLCs, HMIs) that are vulnerable to exploitation if stolen.
Solution: Secret Server can centrally vault and rotate credentials for OT devices, such as SCADA systems or industrial controllers, ensuring that only authorized personnel or automated processes can access them.
How Delinea Solves This: Delinea Secret Server eliminates hardcoded and static credentials by storing them in an encrypted vault, automatically rotating them on a schedule or after use, and enforcing Multi-Factor Authentication (MFA) for retrieval.
Benefit: Minimizes the attack surface by eliminating static, predictable passwords and provides an audit trail of credential usage, enhancing compliance with standards like NIST 800-82 or IEC 62443.
Challenge: Insider threats or compromised accounts in OT environments can lead to unauthorized changes to industrial processes, such as altering pump settings in a water treatment plant.
Solution: Privileged Behavior Analytics establishes a baseline of normal activity for OT administrators and service accounts (e.g., those managing DCS systems).
How Delinea Solves This: Delinea leverages machine learning to analyze patterns of privileged account usage in real-time, correlating OT-specific actions (e.g., logins to HMIs) with contextual data like time, location, and device type.
Benefit: Enables early detection of malicious activity or misconfigurations in OT environments, preventing operational disruptions or safety incidents.
Challenge: OT servers running SCADA software or historian databases are often exposed to IT-OT convergence risks, such as lateral movement from a compromised IT system.
Solution: Server PAM enforces just-in-time (JIT) and just-enough privilege for OT server access. For example, an engineer updating a control server in an oil refinery would receive temporary elevated privileges only for the task duration, with the session recorded for auditing.
How Delinea Solves This: Delinea Server PAM uses a proxy-based architecture to mediate access, enforcing granular policies that limit privileges to specific tasks and timeframes.
Benefit: Reduces the risk of unauthorized access or malware propagation to OT servers while maintaining operational uptime and regulatory compliance.
Challenge: IIoT devices and automated OT systems (e.g., robotic assembly lines) often use embedded secrets or API keys that, if exposed, could allow attackers to manipulate production processes.
Solution: DevOps Secrets Vault securely manages and injects secrets into OT automation scripts or IIoT device communications.
How Delinea Solves This: Delinea provides a lightweight, API-driven vault that generates short-lived, unique secrets for each
transaction, eliminating persistent credentials in code or device memory.
Benefit: Protects automated OT processes from credential theft, ensuring secure machine-to-machine communication in Industry 4.0 environments.
Challenge: Third-party vendors or temporary contractors in OT environments (e.g., maintenance crews for power grids) often retain access longer than necessary, increasing risk.
Solution: Account Lifecycle Manager automates the creation and removal of privileged accounts for
OT systems. For example, a vendor repairing a wind turbine’s control system could be granted temporary access that automatically expires after the job, with all actions logged.
How Delinea Solves This: Delinea automates account workflows using role-based policies, integrating with HR systems or ticketing tools to trigger provisioning/deprovisioning.
Benefit: Prevents orphaned accounts and ensures least privilege, reducing the risk of unauthorized access to critical OT infrastructure.
Challenge: Remote access to OT systems (e.g., for monitoring a pipeline) is a common attack vector due to weak authentication or unmonitored sessions.
Solution: Connection Management enables secure, audited remote access to OT assets like HMIs or RTUs.
How Delinea Solves This: Delinea deploys a secure gateway that proxies remote connections, requiring MFA and enforcing zero-trust policies.
Benefit: Secures remote maintenance and monitoring while preventing unauthorized entry, aligning with zero-trust principles for OT.
Challenge: OT environments often lack standardized access policies, leading to over-privileged users who can unintentionally or maliciously disrupt operations (e.g., altering settings on a chemical reactor).
Solution: Policy and Governance defines and enforces role-based access for OT personnel.
How Delinea Solves This: Delinea centralizes policy management in a single console, applying granular controls (e.g., command whitelisting) across OT systems.
Benefit: Ensures least privilege and operational safety by limiting what users can do, reducing human error and insider threat risks.
Legacy System Vulnerabilities: Delinea vaults credentials and enforces least privilege with minimal disruption, using agentless or lightweight integrations tailored to legacy OT protocols.
IT-OT Convergence: Delinea’s session monitoring and behavior analytics detect and block threats at the IT-OT boundary, leveraging real time analytics and zero-trust access controls.
Regulatory Compliance: Delinea generates tamper-proof audit logs and enforces access controls that meet OT standards like NERC CIP, ISA/IEC 62443, and NIS Directive, with reporting tools for auditors.
Real-Time Operations: Delinea’s JIT access and high-speed vaulting ensure low-latency security that aligns with OT’s uptime requirements, avoiding interference with critical processes.
Conclusion
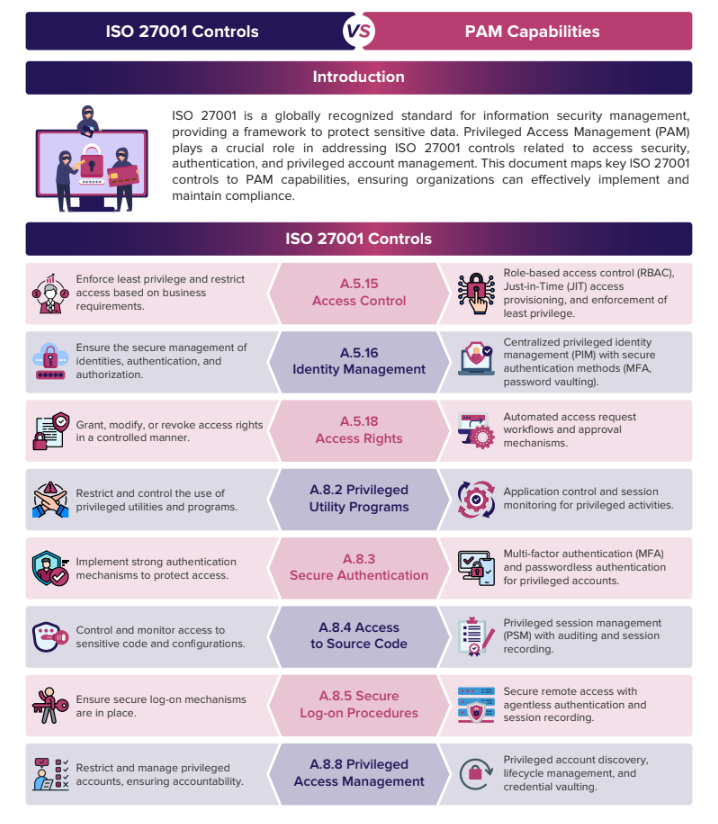
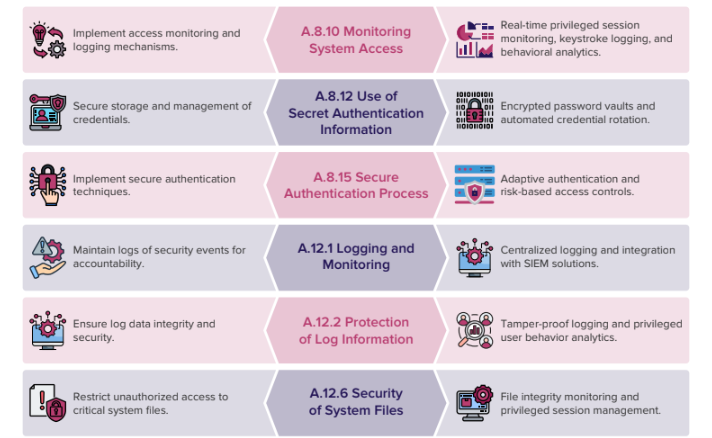
Implementing PAM solutions aligned with ISO 27001 controls helps organizations enhance their security posture, reduce attack surfaces, and ensure compliance. By integrating PAM capabilities, organizations can eectively manage privileged access, enforce least privilege, and maintain audit readiness.
Next Steps:
1. Conduct a PAM maturity assessment
aligned with ISO 27001.
2. Implement automated access control mechanisms.
3. Establish continuous monitoring
and audit practices.

In order to guarantee security and accountability, effective privileged remote access solutions frequently incorporate features like multi-factor authentication (MFA), audit logging, and session recording.

By capturing and reviewing the actions made by privileged users during their sessions, session recording enables organizations to provide a thorough audit trail for forensic analysis and compliance.

Audit logging helps organizations identify suspicious activity and take quick action in the event of a security incident by keeping track of all operations and access attempts made by privileged users.

By demanding several forms of verification (such as passwords and biometrics) before giving access to privileged accounts, MFA adds an extra layer of protection and lowers the possibility of illegal access due to stolen credentials.

- Privilege remote access solutions are essential for preserving operational continuity and fending off cyberattacks in today's networked and increasingly remote work environments.
- Regardless of the users' or the systems' physical locations, they let security teams and IT managers handle privileged accounts safely.
- Organizations may improve their overall cybersecurity posture, reduce the risk of external attacks and internal threats, and guarantee the integrity and confidentiality of their most important data and assets by putting strong privileged remote access procedures in place.
YouTube
OATH OTP MFA Explained: Easy Setup Guide for Stronger Security
About Me
Bert Blevins is a distinguished technology entrepreneur and educator who brings together extensive technical expertise with strategic business acumen and dedicated community leadership. He holds an MBA from the University of Nevada Las Vegas and a Bachelor’s degree in Advertising from Western Kentucky University, credentials that reflect his unique ability to bridge the gap between technical innovation and business strategy.
As a Certified Cyber Insurance Specialist, Mr. Blevins has established himself as an authority in information architecture, with particular emphasis on collaboration, security, and private blockchain technologies. His comprehensive understanding of cybersecurity frameworks and risk management strategies has made him a valuable advisor to organizations navigating the complex landscape of digital transformation. His academic contributions include serving as an Adjunct Professor at both Western Kentucky University and the University of Phoenix, where he demonstrates his commitment to educational excellence and knowledge sharing. Through his teaching, he has helped shape the next generation of technology professionals, emphasizing practical applications alongside theoretical foundations.

In his leadership capacity, Mr. Blevins served as President of the Houston SharePoint User Group, where he facilitated knowledge exchange among technology professionals and fostered a community of practice in enterprise collaboration solutions. He further extended his community impact through director positions with Rotary International Las Vegas and the American Heart Association’s Las Vegas Chapter, demonstrating his commitment to civic engagement and philanthropic leadership. His specialized knowledge in process optimization, data visualization, and information security has proven instrumental in helping organizations align their technological capabilities with business objectives, resulting in measurable improvements in operational efficiency and risk management.
Mr. Blevins is recognized for his innovative solutions to complex operational challenges, particularly in the realm of enterprise architecture and systems integration. His consulting practice focuses on workplace automation and digital transformation, guiding organizations in the implementation of cutting-edge technologies while maintaining robust security protocols. He has successfully led numerous large-scale digital transformation initiatives, helping organizations modernize their technology infrastructure while ensuring business continuity and regulatory compliance. His expertise extends to emerging technologies such as artificial intelligence and machine learning, where he helps organizations identify and implement practical applications that drive business value.

As a thought leader in the technology sector, Mr. Blevins regularly contributes to industry conferences and professional forums, sharing insights on topics ranging from cybersecurity best practices to the future of workplace automation. His approach combines strategic vision with practical implementation, helping organizations navigate the complexities of digital transformation while maintaining focus on their core business objectives. His work in information security has been particularly noteworthy, as he has helped numerous organizations develop and implement comprehensive security frameworks that address both technical and human factors.
Beyond his professional pursuits, Mr. Blevins is an accomplished endurance athlete who has participated in Ironman Triathlons and marathons, demonstrating the same dedication and disciplined approach that characterizes his professional work. He maintains an active interest in emerging technologies, including drone operations and virtual reality applications, reflecting his commitment to staying at the forefront of technological advancement. His personal interests in endurance sports and cutting-edge technology complement his professional expertise, illustrating his belief in continuous improvement and the pursuit of excellence in all endeavors.